About Comp AI Device Agent
Comp AI Device Agent is a lightweight desktop application that runs in your system tray and automatically monitors your device’s security compliance. It checks your device configuration every hour and reports the results to your organization’s Comp AI portal. The agent checks four security areas:| Security Check | What It Verifies |
|---|---|
| Disk Encryption | FileVault (macOS), BitLocker (Windows), or LUKS (Linux) is enabled |
| Antivirus | Active antivirus protection (XProtect, Windows Defender, ClamAV, etc.) |
| Password Policy | Minimum 8-character password enforced at the OS level |
| Screen Lock | Automatic screen lock activates within 5 minutes of inactivity |
The agent runs silently in your system tray and uses minimal system resources. It does not collect personal data, browsing history, or file contents.
System Requirements
| Requirement | Details |
|---|---|
| Operating Systems | macOS 14+, Windows 10+, Linux (Ubuntu 20.04+) |
| Memory | 512MB RAM minimum |
| Storage | 200MB available disk space |
Installation
Step 1: Download the Agent
Step 1: Download the Agent
Log in to your organization’s Employee Portal and navigate to the Device Agent task. Click Download Agent to get the installer for your operating system.
- macOS: Downloads a
.dmgfile. If you have an Apple Silicon Mac (M1/M2/M3/M4), the portal selects the correct version automatically. You can also switch between Apple Silicon and Intel using the dropdown. - Windows: Downloads a
.exeinstaller. - Linux: Downloads a
.debpackage.
Step 2: Install the Agent
Step 2: Install the Agent
macOS: Double-click the downloaded
.dmg file and drag the Comp AI Device Agent to your Applications folder.Windows: Double-click the downloaded .exe file and follow the installation wizard.Linux: Install the downloaded .deb package using your package manager or by double-clicking it:Step 3: Sign In
Step 3: Sign In
After installation, the agent opens a sign-in window. Log in with your work email using the same method you use for the Employee Portal (email OTP, Google, or Microsoft).

- Registers your device with your organization(s)
- Runs the first compliance check immediately
- Starts checking every hour in the background
Using the Device Agent
After signing in, the agent lives in your system tray (menu bar on macOS, system tray on Windows/Linux). Click the tray icon to open the status window.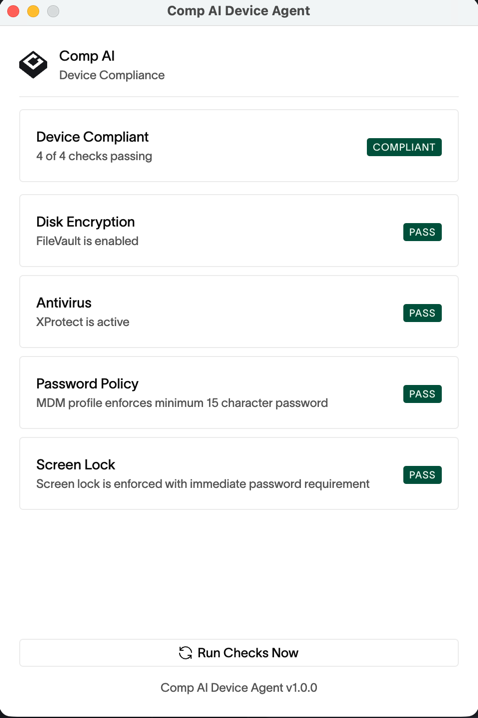
- Compliance status — whether your device is compliant or needs attention
- Individual checks — each of the four security checks with Pass/Fail status
- Remediation options — for any failing check, the agent offers a way to fix it
Tray Icon Status
| Icon Color | Meaning |
|---|---|
| Green | Device is compliant — all checks passing |
| Red | Device is non-compliant — one or more checks failing |
| Gray | Agent is not signed in or checks are loading |
Fixing Failing Checks
When a check fails, the agent provides remediation options depending on what can be done automatically:| Option | Description |
|---|---|
| Fix | The agent fixes the issue automatically |
| Fix (Admin) | The agent fixes it but may prompt for your system password |
| Open Settings | Opens the relevant OS settings pane so you can fix it manually |
| View Guide | Shows step-by-step instructions to resolve the issue |
Tray Menu Options
Right-click (or click on macOS) the tray icon to access:- Run Checks Now — trigger an immediate compliance check
- View Details — open the status window
- Start at Login — toggle whether the agent launches automatically when you log in (enabled by default)
- Sign Out — sign out of the agent
- Quit — close the agent completely
Verifying on the Portal
After the agent runs its first check, you can verify your device compliance status on the Employee Portal. The Device Agent task shows your device name, platform, and whether all security checks are passing. The portal updates automatically — it polls your device status every 30 seconds while the page is open.Troubleshooting
Agent won't sign in
Agent won't sign in
- Make sure you’re using the same email address you use for the Employee Portal
- Check your internet connection
- Try quitting the agent completely and reopening it
- If using Google or Microsoft sign-in, make sure popups are not blocked
Checks are failing unexpectedly
Checks are failing unexpectedly
- Click Run Checks Now to refresh the results
- Review the failing check details — the agent shows what it detected
- Use the remediation option provided (Fix, Open Settings, or View Guide)
- Some changes (like enabling FileVault) require a restart to take effect
Agent is not visible in the system tray
Agent is not visible in the system tray
- macOS: Look in the menu bar at the top of your screen. The icon may be hidden — check the overflow area (click the
>>or similar) - Windows: Click the up arrow in the system tray to see hidden icons
- Linux: Check your desktop environment’s system tray or notification area
- The agent may need to be reopened from your Applications folder
Portal shows device as non-compliant even though agent shows all checks passing
Portal shows device as non-compliant even though agent shows all checks passing
- Wait up to 30 seconds for the portal to refresh
- Click Run Checks Now in the agent to trigger a fresh report
- Check that the agent is signed in (tray icon should be green, not gray)
Migrating from FleetDM
If your device previously had the FleetDM agent (fleetd) installed, you should uninstall it after setting up the new Comp AI Device Agent. The new agent fully replaces FleetDM, and having both running is unnecessary. Follow the official uninstall guide for your platform: How to uninstall fleetdManual Evidence Collection
For users who cannot install the agent on their device, manual evidence of device settings is required. Below are the required pieces of evidence and where to obtain them.Windows Manual Evidence
Windows Manual Evidence
Windows 10 & 11
Enable BitLocker- Press Start → type Manage BitLocker → open it.
Take a screenshot of the BitLocker Drive Encryption window showing “On” for the C: drive. - Select the drive (usually C:) → click Turn on BitLocker.
- Save the recovery key to Microsoft Account / USB / secure location.
- Restart if prompted.
- Press Start → Settings → Personalization → Lock screen.
- Scroll down → click Screen timeout settings.
Take a screenshot showing the screen timeout set to 5 minutes. - Set Screen turns off = 5 minutes.
- In Settings → Accounts → Sign-in options → ensure Require sign-in is set to “When PC wakes up from sleep”.
Take a screenshot of the Sign-in Options page showing this setting.
- Press Win + R, type
secpol.msc, press Enter. - Go to Account Policies → Password Policy.
- Set Minimum password length = 8+.
Take a screenshot of the Password Policy window with “Minimum password length” = 8 or more.
- Settings → Update & Security → Windows Update.
- Select Advanced options → make sure Automatic updates are enabled.
Take a screenshot of the Windows Update settings page showing automatic updates turned on.
- Settings → Update & Security → Windows Security.
- Open Virus & threat protection → ensure Real-time protection is on.
Take a screenshot of the Windows Security window showing Real-time protection is ON.
Evidence gathered manually will be uploaded as a comment and attachment to the “Secure Devices” and “Device List” tasks with the user’s email of the device the evidence is for.
macOS Manual Evidence
macOS Manual Evidence
macOS (Monterey, Ventura, Sonoma, Sequoia)
Enable FileVault- Open System Settings (or System Preferences in older versions).
- Go to Privacy & Security → FileVault.
- Click Turn On FileVault → enter password.
- Record recovery key.
Take a screenshot of the FileVault settings page showing “FileVault is enabled for the disk.”
- System Settings → Lock Screen.
- Set Start screen saver when inactive = 5 minutes.
Take a screenshot showing the setting at 5 minutes. - Set Require password after sleep or screen saver begins = Immediately.
Take a screenshot showing “Require password immediately” is selected.
- Native macOS UI doesn’t enforce this; requires Terminal or MDM.
pwpolicy -setglobalpolicy "minChars=8"- If set via Terminal, take a screenshot of the command output confirming the policy.
- If enforced by MDM (Jamf, Intune, etc.), screenshot the compliance screen from the MDM portal.
- System Settings → General → Software Update.
- Click Automatic Updates → enable all options (Install Security Responses & System files, etc.).
Take a screenshot of the Automatic Updates options screen with all toggles enabled.
- macOS automatically runs XProtect in the background.
- Simply ensure macOS is fully updated.
Take a screenshot of the Software Update page showing the Mac is up to date.
Evidence gathered manually will be uploaded as a comment and attachment to the “Secure Devices” and “Device List” tasks with the user’s email of the device the evidence is for.
Linux Manual Evidence
Linux Manual Evidence
Ubuntu 20.04+ / Debian-based
Enable LUKS Disk Encryption- LUKS encryption is typically configured during OS installation.
- To verify, run:
lsblk -o NAME,TYPE,FSTYPE | grep crypt
Take a screenshot showing the encrypted volume.
- Open Settings → Privacy → Screen Lock.
- Set Automatic Screen Lock Delay = 5 minutes.
Take a screenshot showing the screen lock delay setting.
- Check minimum password length:
grep PASS_MIN_LEN /etc/login.defs - Ensure it’s set to 8 or higher.
Take a screenshot of the output.
- Verify ClamAV or another antivirus is installed and running:
- Alternatively, show AppArmor or SELinux is enforcing:
Take a screenshot of the output showing active protection.
Evidence gathered manually will be uploaded as a comment and attachment to the “Secure Devices” and “Device List” tasks with the user’s email of the device the evidence is for.

